In the fast-paced world of cloud computing, ensuring the security of your infrastructure is paramount. One critical aspect of cloud security is the management of security groups in Amazon Web Services (AWS). A misconfigured security group can expose your resources to unauthorized access and potentially lead to a security breach. That’s where AWS Alert comes into play—providing real-time notifications whenever there are changes to your security groups, allowing you to stay one step ahead of potential threats.
Understanding AWS Alert for Security Group Changes
AWS Alert is an essential tool that helps monitor any adjustments made to your security groups. These groups serve as virtual firewalls that control the inbound and outbound traffic to your instances. By setting up real-time alerts, AWS ensures that you are immediately informed of any modifications, be they accidental or malicious. Such alerts enable administrators to react promptly, ensuring the safety and integrity of your cloud environment.
Why Are Security Group Changes Important?
Security groups act as gatekeepers for your AWS instances. Any change in their configuration—such as altering inbound or outbound rules—can affect the security posture of your infrastructure. Unauthorized modifications could expose critical systems to public access, while restrictive changes could interrupt service delivery.
Having AWS Alerts configured to notify you of these changes allows your security teams to take immediate corrective action. Whether it’s modifying a rule, reviewing an unexpected change, or launching a full-scale investigation, the ability to respond quickly is crucial in maintaining a secure environment.
How AWS Alert Works for Security Group Monitoring
AWS Alert leverages AWS services like Amazon CloudWatch, AWS CloudTrail, and AWS Lambda to detect and notify administrators about any security group modifications in real-time. Here’s how the process typically works:
-
Tracking Changes with AWS CloudTrail:
AWS CloudTrail logs all API calls made within your AWS account, including those that modify security group settings. By analyzing CloudTrail logs, AWS Alert can detect any changes and trigger an alert.
-
Real-Time Monitoring via Amazon CloudWatch:
CloudWatch monitors operational metrics and logs, including the activity recorded by CloudTrail. By setting up CloudWatch Alarms, administrators can receive real-time notifications about security group changes.
-
Automation with AWS Lambda:
Once an alert is triggered, AWS Lambda can be used to automate responses, such as reverting unauthorized changes or notifying administrators through email or SMS.
Together, these services provide a robust system for monitoring and alerting on security group changes, ensuring that your infrastructure remains protected.
Benefits of Using AWS Alert for Security Group Changes
Setting up AWS Alert for monitoring security group changes brings numerous benefits to organizations, particularly those with stringent security requirements. Here are some key advantages:
-
Improved Security Posture:
Real-time alerts provide you with immediate awareness of any security group modifications, enabling you to take quick corrective actions to prevent potential vulnerabilities.
-
Enhanced Compliance:
Many regulatory frameworks, such as PCI DSS and GDPR, require continuous monitoring of security controls. AWS Alerts help meet these compliance requirements by ensuring that all changes to security groups are tracked and responded to promptly.
-
Operational Efficiency:
With AWS Alert, your team no longer needs to manually monitor security group changes. Automated alerts allow you to focus on more critical tasks while being confident that any security group modifications are under control.
-
Auditable Logs:
By utilizing CloudTrail, you maintain a detailed log of all changes to your security groups, which is useful for both security audits and investigations. These logs can be stored in Amazon S3, ensuring you have a historical record of all changes.
Best Practices for Setting Up AWS Alert
When setting up AWS Alert to monitor security group changes, it’s essential to follow best practices to ensure maximum security and efficiency. Here’s a step-by-step guide:
-
Enable CloudTrail for All Regions:
Ensure that AWS CloudTrail is enabled in every AWS region where your organization operates. This allows you to capture all activity related to security group changes, even if they occur outside of your primary regions.
-
Set Up CloudWatch Alarms:
Create CloudWatch Alarms to trigger alerts when specific API actions related to security groups (such as AuthorizeSecurityGroupIngress or RevokeSecurityGroupEgress) are detected. Be sure to configure notifications via email or SMS.
-
Use AWS Lambda for Automated Responses:
Automate the remediation of unauthorized changes using AWS Lambda. For example, if a security group is modified to allow access from an unapproved IP range, Lambda can automatically revert the change and notify administrators.
-
Integrate with AWS SNS for Alert Distribution:
AWS Simple Notification Service (SNS) can be used to distribute alerts to multiple channels, including email, SMS, or third-party monitoring tools like PagerDuty or Slack. This ensures that your team is promptly notified no matter where they are.
-
Establish IAM Policies for Least Privilege Access:
Use AWS Identity and Access Management (IAM) to enforce least privilege access to security groups. Only allow authorized personnel to modify security group settings, reducing the risk of accidental or malicious changes.
Real-World Use Cases for AWS Alert
To illustrate the effectiveness of AWS Alert for security group changes, let’s explore a couple of real-world scenarios:
-
Scenario 1: Accidental Misconfiguration
A developer mistakenly modifies a security group to allow unrestricted inbound access from the internet. AWS Alert immediately notifies the security team, which then swiftly reverts the change, preventing a potential security incident.
-
Scenario 2: Suspicious Activity Detection
In another case, an unauthorized user attempts to modify a security group, exposing critical resources to the public. The real-time alert triggered by AWS Alert enables the security team to investigate the breach, isolate the compromised account, and secure the infrastructure.
Ensuring the security of your assets and data is of utmost importance. With the increasing number of cyber threats, it’s essential to stay ahead of the game and stay informed of any suspicious activity on your AWS environment. AWS provides a range of security-related features and services, one of which is the ability to set up real-time alerts for security group events that occur within your environment.
To Implement the alert we require CloudTrail, CloudWatch, SNS,Lambda
Navigating the Cloud Made Easy – Connect with Our Expert for Tailored Solutions!
STEPS:
1.Creating a Trail by navigating to Cloudtrail.
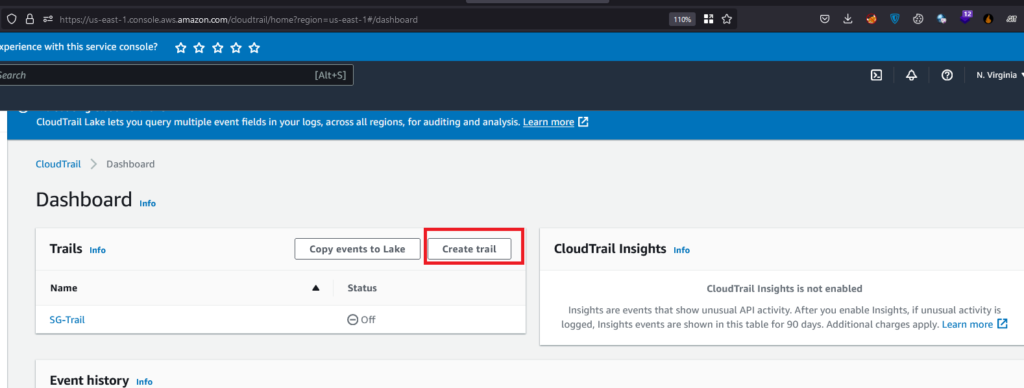
2. Now we are going to create SNS Topic and Subscription

3.Then we are creating a Cloudwatch rule for any inbound rule added to the security group.
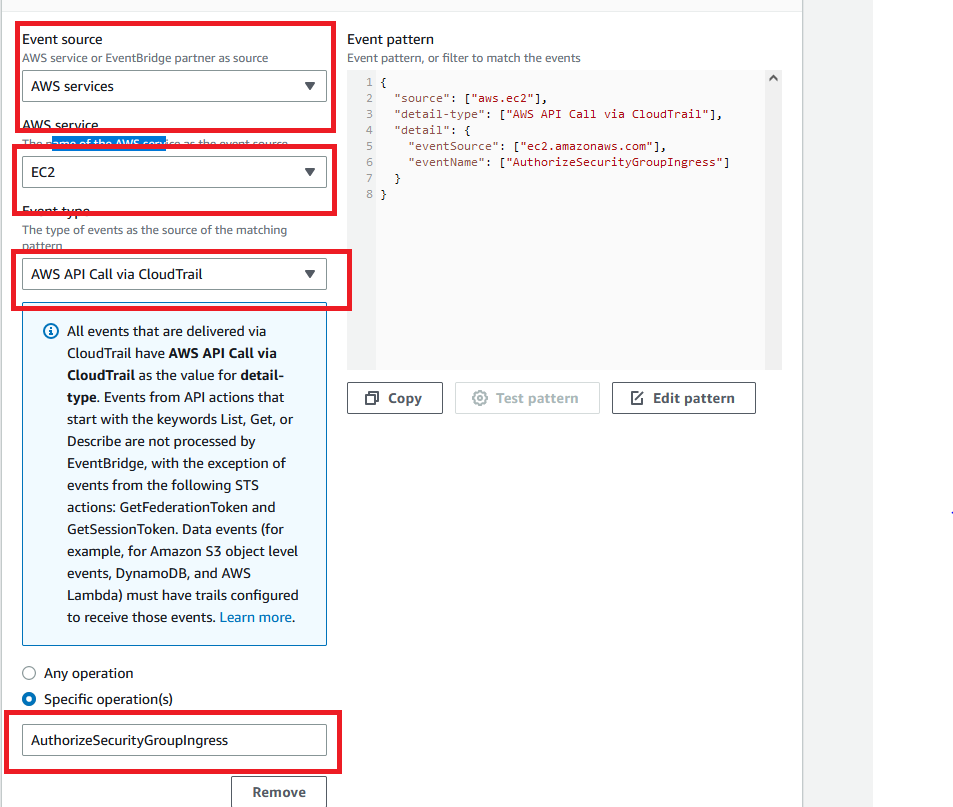
set the targets to the SNS that we had previously created.
4. Now we are going to create a Lambda function for slack notification. Add a trigger to SNS and replace the webhook URL.
import urllib3
import json
http = urllib3.PoolManager()
def lambda_handler(event, context):
url = "https://hooks.slack.com/services/yourwebhookurl"
msg = {
"channel": "yourchannel",
"text": event["Records"][0]["Sns"]["Message"],
"icon_emoji": "",
}
encoded_msg = json.dumps(msg).encode("utf-8")
resp = http.request("POST", url, body=encoded_msg)
print(
{
"message": event["Records"][0]["Sns"]["Message"],
"status_code": resp.status,
"response": resp.data,
})
Our simple real-time security alert is ready.
Learn more about Cloudtrail.
