In today’s digital world, security is paramount. With the rise of cloud applications, mobile platforms, and APIs, developers increasingly rely on JSON Web Tokens (JWT) to ensure secure communication between clients and servers.
However, JWTs are not immune to vulnerabilities, which is why pentesting JWT has become an essential part of modern cybersecurity practices. In this blog post, we’ll explore five critical insights for securing your JWT through pentesting techniques, ensuring your systems remain safe from potential exploits.
What is JWT ?
JWT stands for JSON Web Token, an open standard designed for securely sharing information between a client and a server. Each JWT consists of encoded JSON objects that contain a set of claims. These tokens are signed using a cryptographic algorithm to ensure the integrity of the claims, preventing any alterations after the token has been issued.
Protect Your Business with Cutting-Edge Cybersecurity Services – Safeguard Your Data 24/7!
Structure of JWT ?
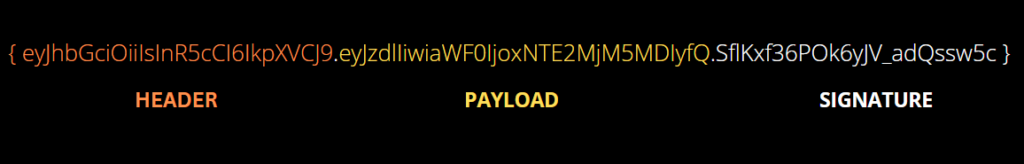
JWT Token consist of : HEADER, PAYLOAD, SIGNATURE
HEADER: The Header consist of “Type” and “algorithm” TYPE denotes to token which is “JWT” and signing algorithm being used, such as HMAC SHA256 or RSA
PAYLOAD: The payload consist of claims (claims are statements).
The types of claims are as follow:-
- Registered: Registered claims are predefined and recommended for use, though they are not mandatory. These claims help provide a set of useful and interoperable information. Examples include
iss (issuer), exp (expiration time), sub (subject), and aud (audience).
- Public: Public claims are custom claims meant for public consumption and should be collision-resistant. These claims may include generic information, such as the user’s name and email address.
- Private: These are the custom claims created to share information between parties that agree on using them and are neither registered or public claims.
SIGNATURE: The Signature of a JWT contains its cryptographic signature, composed of the base64 URL-encoded header and payload segments.
Why is Pentesting JWT Crucial for Security?
Conducting pentesting JWT ensures that the system’s use of JWTs is robust and secure. By identifying potential weaknesses in the way JWTs are generated, validated, and managed, pentesters can prevent common security issues like token expiration bypass, weak encryption algorithms, and insecure claims.
1. Focus on Algorithm Vulnerabilities During Pentesting JWT
One of the most crucial insights when conducting pentesting JWT is to thoroughly examine the algorithm used to sign the token. JWT supports multiple algorithms such as HS256 (HMAC with SHA-256) and RS256 (RSA signature with SHA-256). However, if improperly configured, an attacker could exploit these algorithms.
Common Algorithm Vulnerabilities:
- None Algorithm Attack: In some cases, if the JWT implementation allows the “none” algorithm, an attacker could manipulate the token header to bypass signature verification altogether. This allows the attacker to issue unauthorized requests.
- Algorithm Confusion: When a server uses RS256 for JWTs, attackers might try to trick the server into accepting an HMAC (HS256) signature instead, which could lead to signature spoofing.
Pentesting JWT should include testing for the improper handling of algorithms and enforcing strong signature verification processes.
Mitigation Techniques:
- Always specify the expected signing algorithm on the server-side.
- Reject JWTs that use the “none” algorithm.
- Ensure that algorithm confusion is not possible by validating that the algorithm used in the JWT header matches the expected one.
2. Examining JWT Claims during Pentesting JWT
JWTs carry a payload known as “claims” that describe the token’s context, such as the user identity (sub), expiration (exp), and issued time (iat). Pentesters should analyze these claims for vulnerabilities during pentesting JWT.
Potential Risks in JWT Claims:
- Token Expiry Issues: Attackers can manipulate the
exp (expiration) claim to extend the lifespan of a JWT, allowing them to access resources beyond the token’s intended validity.
- Insecure Claims: Sensitive data, like user roles or permissions, should not be embedded in JWT claims without encryption, as attackers can easily read and modify the data.
Pentesting JWT should include checking how claims are handled to ensure no sensitive information is exposed and that expiration claims cannot be tampered with.
Mitigation Techniques:
- Use short-lived tokens and refresh tokens to ensure minimal exposure if a token is compromised.
- Avoid embedding sensitive information in JWT claims.
- Ensure proper claim validation on the server side, especially for time-related claims (
exp, iat, nbf).
3. Securing Token Storage and Transmission in Pentesting JWT
During pentesting JWT, it’s essential to evaluate how tokens are stored and transmitted between the client and the server. Insecure storage or transmission of tokens opens up significant vulnerabilities, including token theft and replay attacks.
Common Storage and Transmission Vulnerabilities:
- Local Storage Vulnerability: Storing JWTs in browser
localStorage can expose tokens to XSS (Cross-Site Scripting) attacks, allowing attackers to steal the token.
- Insecure Transmission: If tokens are transmitted over an unencrypted connection (HTTP), they can be intercepted by attackers using man-in-the-middle (MITM) techniques.
Mitigation Techniques:
- Store tokens in HTTP-only cookies instead of localStorage to protect against XSS attacks.
- Always use HTTPS for transmitting JWTs to ensure secure communication between the client and server.
- Implement token rotation strategies to reduce the impact of token theft.
4. Testing for Replay Attacks in Pentesting JWT
Replay attacks occur when an attacker intercepts a valid JWT and reuses it to gain unauthorized access to protected resources. Pentesting JWT should include testing for potential replay attacks, especially in systems that rely heavily on JWT-based authentication.
How Replay Attacks Work:
An attacker can capture a JWT through network sniffing (especially over insecure HTTP connections) and use it to authenticate multiple times without the server realizing that the token has been compromised.
Mitigation Techniques:
- Use of One-Time Tokens: Implement one-time use tokens or add unique nonces to tokens to prevent reuse.
- Token Expiry: Use short expiration times for tokens to minimize the window in which a token can be reused.
- IP and Device Binding: Bind tokens to specific IP addresses or devices to limit their use if stolen.
Pentesting JWT should include ensuring these measures are in place to prevent replay attacks.
5. Preventing Brute Force Attacks on JWT Secrets
In pentesting JWT, the strength of the token’s secret is crucial. Weak secrets make it easier for attackers to brute-force or guess the secret key, enabling them to generate or modify JWTs maliciously.
Potential Risks:
- Weak Secrets: If JWT secrets are short or predictable, attackers can use brute-force techniques to guess the key.
- Key Exposure: Poor key management practices, such as hardcoding secrets in code repositories, can lead to secret exposure.
Mitigation Techniques:
- Use long, complex secrets, especially for HMAC algorithms.
- Store secrets securely using environment variables or secret management tools, rather than hardcoding them.
- Regularly rotate secrets and tokens to minimize the risk of exposure.
During pentesting JWT, testers should attempt brute-force attacks to ensure that the secret used for signing tokens is strong and well-protected.
Pen-testing JWT (JSON WEB TOKENS)
Algorithm to None : As JWT supports none algorithm. An attacker can tamper the alg with ‘none’ and login as a legitimate user.
STEPS : Acquire the JWT Token and change the alg to none.
{
"alg" : "none",
"typ" : "JWT"
}
{
"user" : "Admin"
}
Mitigation :It’s possible to acquire a JWT token and alter the algorithm to none. However, using the none algorithm is highly discouraged in production environments.
RS256 to HS256 : When an application utilizes the RS256 algorithm, it uses a private key for signing the token and a public key for verifying it. An attacker might exploit this by creating an HS256 token and signing it with the public key.
STEPS : It’s possible to acquire a JWT token and alter the algorithm to none. However, using the none algorithm is highly discouraged in production environments.
openssl s_client -connect target.com:443 2>&1 < /dev/null | sed -n ‘/—–BEGIN/,/—–END/p’ > certificatechain.pem
openssl x509 -pubkey -in certificatechain.pem -noout > pubkey.pem
Now we can create the own HS256 Token by using JOSEPH Burp extension.
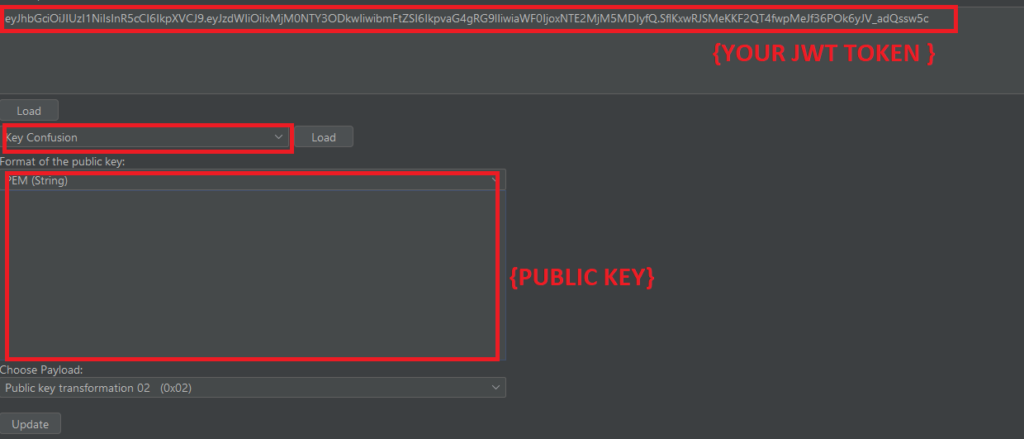
Now we can create the own HS256 Token by using JOSEPH Burp extension.
Mitigation : It’s advisable not to trust HS256 when RS256 is used.
No Signature Verification : In some cases, an application may fail to validate the signature of a JWT. This vulnerability allows an attacker to bypass the security mechanisms.
STEPS : An attacker can get into victims account by removing the signature part from the JWT Token
{
"alg" : "HS256",
"typ" : "JWT"
}
{
"user" : "Admin"
}
Mitigation : It is recommended to validate the signature.
How to prevent JWT attacks ?
Use strong encryption for the payload : To protect the payload, it is recommended to use strong encryption algorithms, such as AES or RSA. This ensures that even if an attacker intercepts the JWT, they cannot read the payload without the appropriate encryption key.
Use secure signature algorithms : Using secure signature algorithms, such as RSA or ECDSA, is crucial in ensuring the integrity and authenticity of the JWT. It is also important to use a strong secret key to prevent brute force attacks on the signature.
Implement proper token management : Proper token management is essential for preventing JWT-related security issues. Tokens should be securely stored, regularly refreshed, and revoked when necessary to prevent unauthorized access. For instance, tokens should be revoked if a user logs out, changes their password, or if there is a suspected security breach.
Validate the JWT on the server-side : It is important to validate the JWT on the server-side to prevent tampering with the payload. This can be achieved by checking the signature, expiration time, and other relevant information before granting access to sensitive information.
Learn more about JSON Web Token (JWT)
