What is the Cyber Kill Chain?
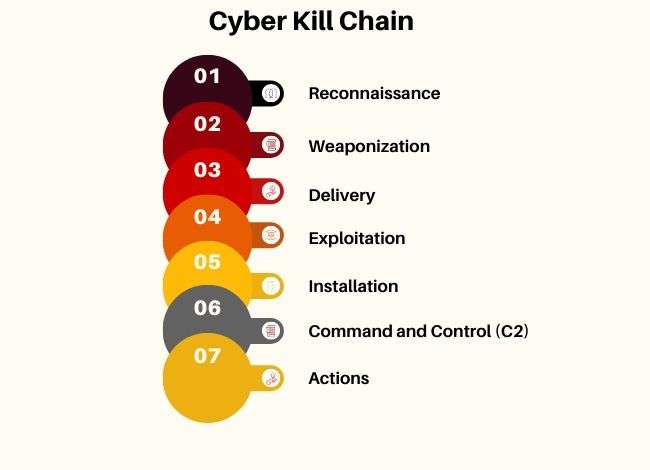
Originally developed by Lockheed Martin, the Cyber Kill Chain consists of:
Reconnaissance – Attackers gather cyber security information about their target.
Weaponization – Malicious software is created using cyber security tools and techniques.
Delivery – The malware is delivered via phishing emails, exploit kits, or other attack vectors.
Exploitation – Vulnerabilities are exploited, compromising systems.
Installation – Malware is installed, granting persistent access.
Command and Control (C2) – Attackers establish remote control.
Actions on Objectives – Data theft, ransomware deployment, or system sabotage occurs.
The Cyber Kill Chain remains a fundamental framework in cybersecurity, outlining the stages of a cyberattack. With the rise of AI in cybersecurity, current cyber security threats, and threat intelligence sources, organizations need to adapt their security measures.
This guide will break down the cyber kill chain, discuss the latest cyber security threats, and explore how AI-driven solutions and threat hunting tools can prevent breaches.
Looking for top-tier cybersecurity solutions? Explore Bornsec’s Services
Evolution of the Cyber Kill Chain
The traditional Cyber Kill Chain framework has evolved due to increasing current cyber security threats and the integration of AI in cybersecurity. Experts now focus on adaptive security models, incorporating cyber threat intelligence sources and threat hunting techniques to counteract sophisticated cyberattacks.
AI’s Role in the Cyber Kill Chain
AI-driven cyber security solutions enhance detection and response by:
Automating threat identification
Strengthening personal cyber security
Improving real-time threat detection
Enhancing threat intelligence reports
As attackers leverage AI for advanced cybercrime, AI tools for cybersecurity help mitigate risks efficiently.
Want to enhance your security framework? Learn More at Bornsec
Common Cyber Kill Chain Attack Vectors
- Ransomware Attacks
Ransomware continues to dominate cybersecurity current events, with the latest ransomware reports highlighting increasing attacks on enterprises. Organizations must implement best cyber security practices to prevent infections.
- Phishing & Social Engineering
Cybercriminals use social engineering to bypass cyber security prevention measures. Recognizing phishing attempts is crucial for cybersecurity for beginners.
- Insider Threats
Malicious insiders can bypass cyber security steps and access sensitive data. Implementing cyber security best practices and cyber security guidelines helps mitigate insider threats.
Threat Hunting Techniques & Tools
Threat hunting involves proactively searching for cyber threats before they escalate. Security professionals use threat hunting tools and cyber security software tools to detect hidden threats.
Top cyber security tools list for threat hunting:
SIEM solutions
EDR (Endpoint Detection & Response)
Best threat intelligence platforms
Cyber threat intelligence certification platforms
Case Study: AI-Driven Cybersecurity Success
A top cyber security company recently deployed AI-driven cyber security solutions to prevent an APT (Advanced Persistent Threat) attack. By integrating cyber security techniques and cyber security monitoring, they neutralized the threat before it escalated.
“AI in cybersecurity is no longer optional; it’s a necessity to counter evolving cyber threats.” – Dr. Jane Mitchell, Cybersecurity Expert
Steps to Strengthen Cyber Defense
To enhance personal cyber security services and corporate defenses, follow these cyber security steps:
Implement free cyber security tools for monitoring.
Train employees on cyber security basics for beginners.
Deploy AI and cybersecurity solutions.
Utilize cyber threat intelligence sources to stay updated.
Conduct regular audits using cyber security playbooks.
Future of the Cyber Kill Chain
With the rise of AI in cybersecurity, the Cyber Kill Chain model will continue evolving. Cybersecurity organizations must adapt to emerging security threats and refine their cybersecurity methods.
For further reading on the Cyber Kill Chain and cyber security updates, explore now.
Conclusion
The Cyber Kill Chain remains a vital cybersecurity model. By leveraging AI-driven cyber security, cyber security tools, and threat intelligence reports, organizations can effectively counter current cyber security threats. Stay proactive, adopt best cyber security practices, and integrate cutting-edge cyber security tools and techniques to safeguard digital assets.