
Zero Day Vulnerability
1. What Is a Zero-Day Vulnerability? A zero-day vulnerability is an undiscovered security flaw within software, hardware, or network infrastructure that remains unknown to the
92% of businesses suffer attacks. Don't wait until it's too late!

1. What Is a Zero-Day Vulnerability? A zero-day vulnerability is an undiscovered security flaw within software, hardware, or network infrastructure that remains unknown to the

What’s Big Data? Big Data refers to extremely large and complex datasets that traditional data- processing tools can not handle effectively. It’s characterized by vast

1. What is IT and OT Security? Understanding the Basics In today’s digital landscape, IT and OT security play a critical role in safeguarding businesses

Denial of Service (DoS) and Distributed Denial of Service (DDoS) Attacks: How to Prevent Them? Introduction: The Rising Threat of DoS & DDoS Attacks The

What Does Code Security Mean? Code security refers to the implementation of best practices, tools, and methodologies to safeguard software applications from vulnerabilities, unauthorized access,

As of February 21, 2025, a prominent topic in cybersecurity is the increasing security risks associated with large language models (LLMs). These AI-driven models have

Payment skimming is a type of cyberattack where criminals steal credit or debit card details during a transaction, often without the victim realizing it. This

What is Endpoint Protection? Endpoint protection refers to cybersecurity solutions designed to safeguard network-connected devices (endpoints) like computers, servers, and mobile devices from cyber threats.

Introduction to Email Security Email security is a crucial aspect of cybersecurity that protects users from various threats such as phishing, malware, and data breaches.
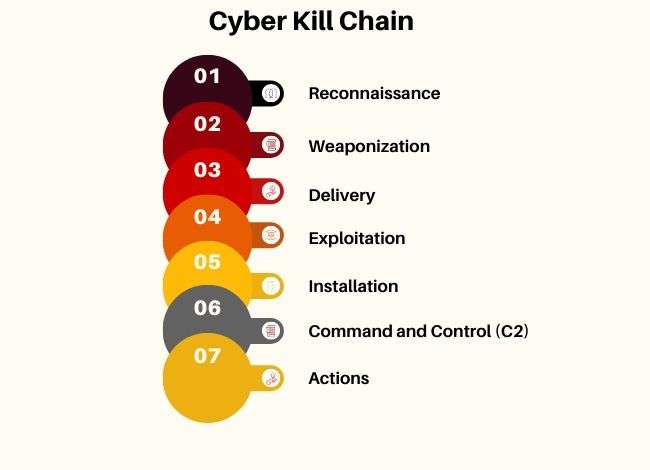
What is the Cyber Kill Chain? Originally developed by Lockheed Martin, the Cyber Kill Chain consists of: Reconnaissance – Attackers gather cyber security information about