
Privileged Access Security (PAS): The Backbone of Modern Cyber Defense
What is Privileged Access? Privileged access refers to special access or abilities above and beyond that of a standard user. These privileges are typically assigned
92% of businesses suffer attacks. Don't wait until it's too late!

What is Privileged Access? Privileged access refers to special access or abilities above and beyond that of a standard user. These privileges are typically assigned

What is Infrastructure Security? Infrastructure security refers to the protection of physical and virtual infrastructure systems from unauthorized access, misuse, malfunction, modification, destruction, or improper

What is Deepfake Social Engineering? Deepfake social engineering refers to a form of manipulation where attackers use deepfake content—AI-generated videos, voices, or images—alongside traditional social

What is an ISO Audit? An ISO audit is a systematic review of an organization’s processes, systems, and operations to determine whether they comply with
What is Web Application Security? Web Application Security refers to the process of protecting web applications from security threats, vulnerabilities, and cyberattacks. It involves using

What Is Encryption? Encryption is the process of converting readable data into an unreadable format using algorithms and keys. Only those with the decryption key
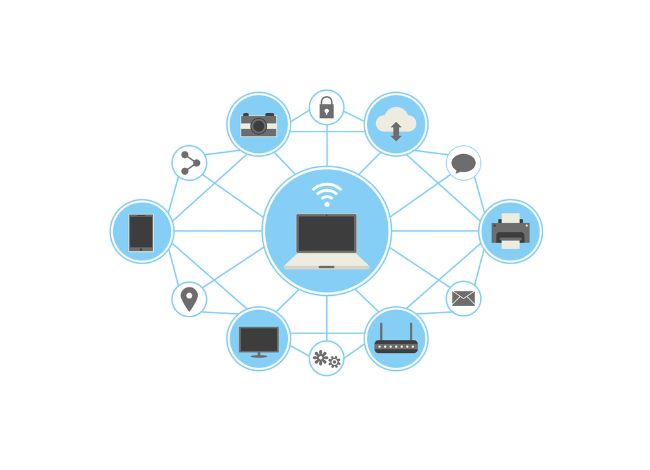
What Are Network Devices? Network devices in computer networks are hardware components that facilitate communication between different devices within a network. These include: Network Routers:
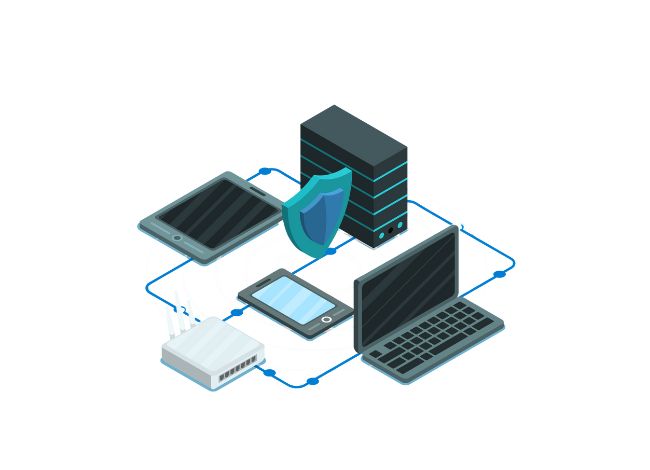
What Is Network Security? Network security refers to the strategies, technologies, and processes used to protect the integrity, confidentiality, and availability of computer networks and

What is the CIA Triad? The CIA Triad is a model designed to guide policies for information security within an organization. It emphasizes three core

Microsoft Teams Security Breach: What You Need to Know Now Cyber security is evolving fast, and so are cyber threats. One of the latest incidents