The Bornsec Blog
Our official blog with cybersecurity news, technology advice, and secure business culture.

ISO On-Site Audit vs. Audit Tools: Why Human Intelligence Still Wins
What is an ISO Audit? An ISO audit is a systematic review of an organization’s processes, systems, and operations to determine whether they comply with
What is Web Application Security?
What is Web Application Security? Web Application Security refers to the process of protecting web applications from security threats, vulnerabilities, and cyberattacks. It involves using

What is encryption?
What Is Encryption? Encryption is the process of converting readable data into an unreadable format using algorithms and keys. Only those with the decryption key
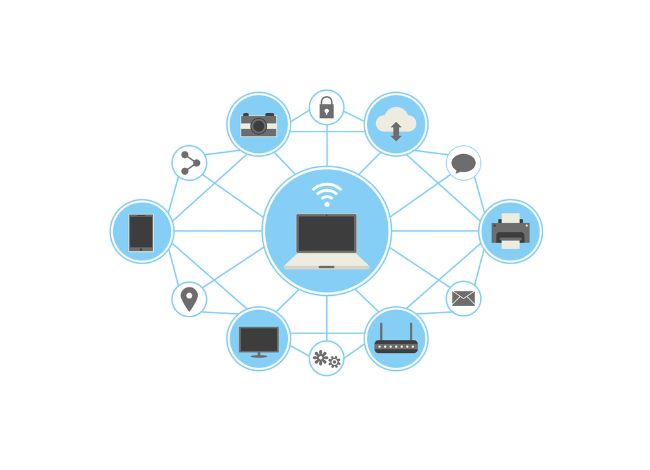
What Are Network Devices?
What Are Network Devices? Network devices in computer networks are hardware components that facilitate communication between different devices within a network. These include: Network Routers:
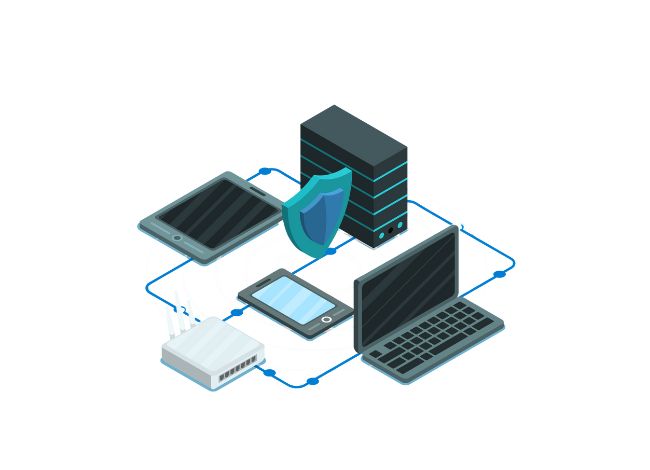
What Is Network Security?
What Is Network Security? Network security refers to the strategies, technologies, and processes used to protect the integrity, confidentiality, and availability of computer networks and

What is the CIA Triad?
What is the CIA Triad? The CIA Triad is a model designed to guide policies for information security within an organization. It emphasizes three core

Microsoft Teams Security Breach: What You Need to Know Now
Microsoft Teams Security Breach: What You Need to Know Now Cyber security is evolving fast, and so are cyber threats. One of the latest incidents

Zero Day Vulnerability
1. What Is a Zero-Day Vulnerability? A zero-day vulnerability is an undiscovered security flaw within software, hardware, or network infrastructure that remains unknown to the

How Big Data Analytics is Transforming the Digital World!
What’s Big Data? Big Data refers to extremely large and complex datasets that traditional data- processing tools can not handle effectively. It’s characterized by vast

IT and OT Security: Bridging the Gap for a Resilient Future
1. What is IT and OT Security? Understanding the Basics In today’s digital landscape, IT and OT security play a critical role in safeguarding businesses
